Yesterday was not a great day. First, I was contacted by one of my gasoline credit card companies that unauthorized charges had been made. Not a huge deal, since I am not liable for these criminal activities, but it is a little inconvenient that I cannot use my card any longer and will have to wait 7-10 days until a new card arrives.
The second event, unrelated to the first, is my website was hacked by another criminal. I am sharing this and what I had to do, in hopes it may help others to avoid my experience.
I have to admit that yesterday wasn’t as bad as the day from hell or the day we lost a wheel. But on to my latest experience as a victim of crime.
I had posted a link to one of my articles on one of the forums over at backpackinglight.com and a friend reported that the link opened up a page full of Japanese characters. Other folks said the link worked, but another friend said there was a problem when he did a Google search for popupbackpacker; some of the links looked they had been hacked.
Below are a couple of examples of what the Google search results looked like.
These pages were a sure sign that PopUpBackpacker.com had probably been hacked. So what does one do if they suspect their site has been hacked, and why should they do something if the site “seems” to work okay?
Google Console
Probably the best way to determine if you site has been hacked is to register your site with Google Console, and follow these instructions from Google on how to determine if your site has been hacked. I have been registered with Google Console (formerly called Google Webmaster Tools) for several years, as I periodically use it to index and optimize my website.
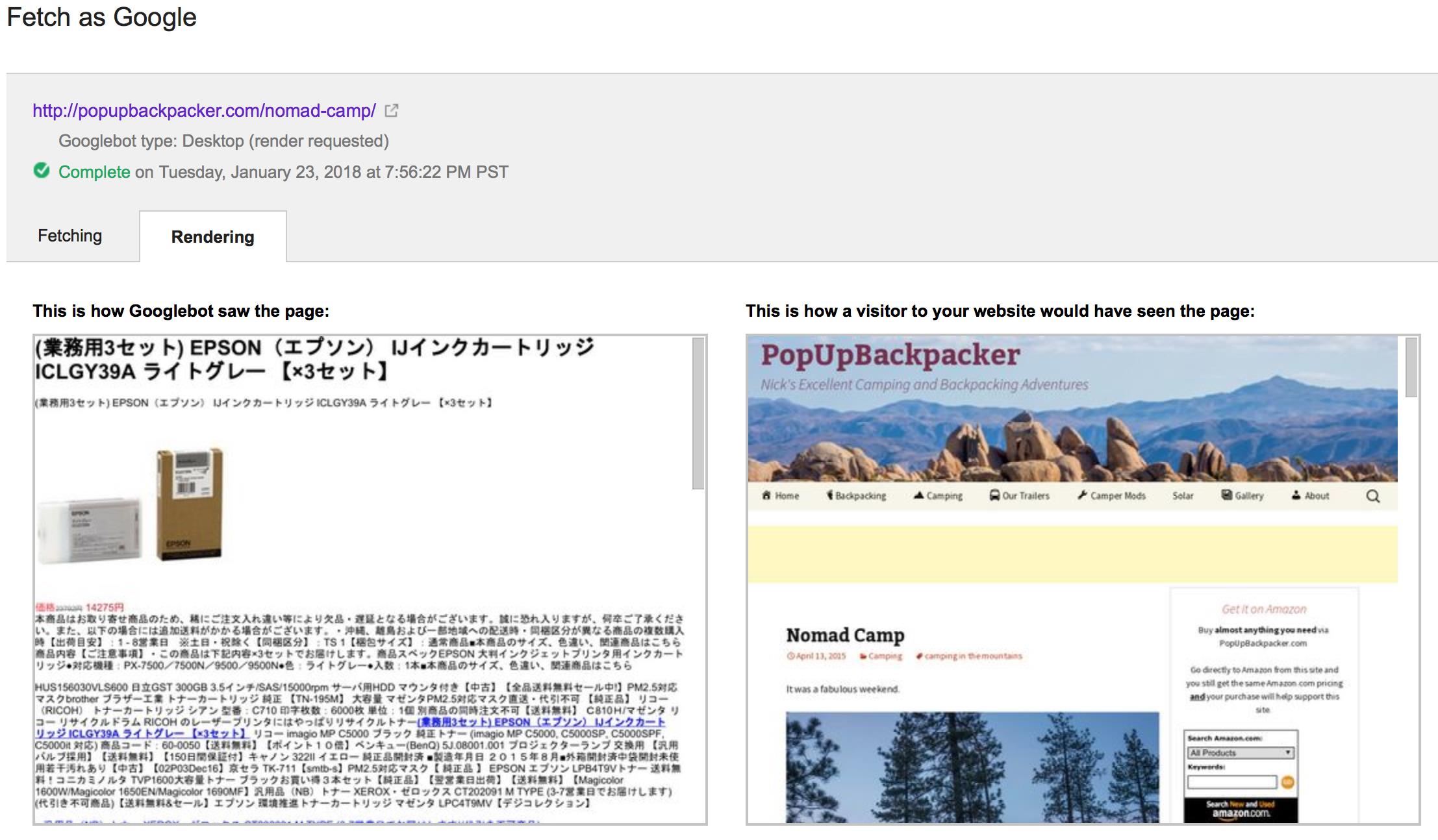
Using the Google Console “Fetch” tool, I was quickly able to see I had many, many problems. From what I found, it looked like most of the issues were hacks that ‘cloaked’ my site. In other words, sometimes my website would not serve up the page link clicked on, but some other page the hacker redirected it to. Below is an example from my Google Console search.
The picture above on the right is a fake link the hacker inserted and some users would see the “404” error on the right, but some users would be directed to the page on the left.
The picture below is similar, but the link to the page on the right exists; so some viewers would be served that page and others the one on the left (below):
Why you should do something if your site is hacked
Worst case scenario is some malicious Malware can erase or make your site unusable. Cloaking could redirect your readers to sites they object to, such as pornographic sites. And lastly a visitor’s browser may block them from accessing your site.
The Steps I Took
Google has a series of videos that explain what a person can do themselves to fix a hacked site. But one needs to be familiar with the programming language and will have to re-write damaged code and/or replace some of the core files and directories, and replace security keys. Although I have modified a lot of the programming code on my website and have some computer programming experience, the task looked somewhat daunting and extremely time intensive. So I started to look at other alternatives.
There are many website Malware tools online, and Google’s tutorials have links to some of these. I ran my website through several of these tools and all of them, except one, found nothing. The exception reported 67 suspicious files. All of these tools are provided by companies that charge to fix hacked sites. I wasn’t comfortable paying any of them. Then I found a site that looked promising: https://www.onehoursitefix.com
ONEHOURSITEFIX
In the end, these folks fixed popupbackpacker.com. What follows is the sequence of events.
On their website, I entered my website address and email. Unlike the other online tools I had used, I got an email back (and it wasn’t asking for money!).
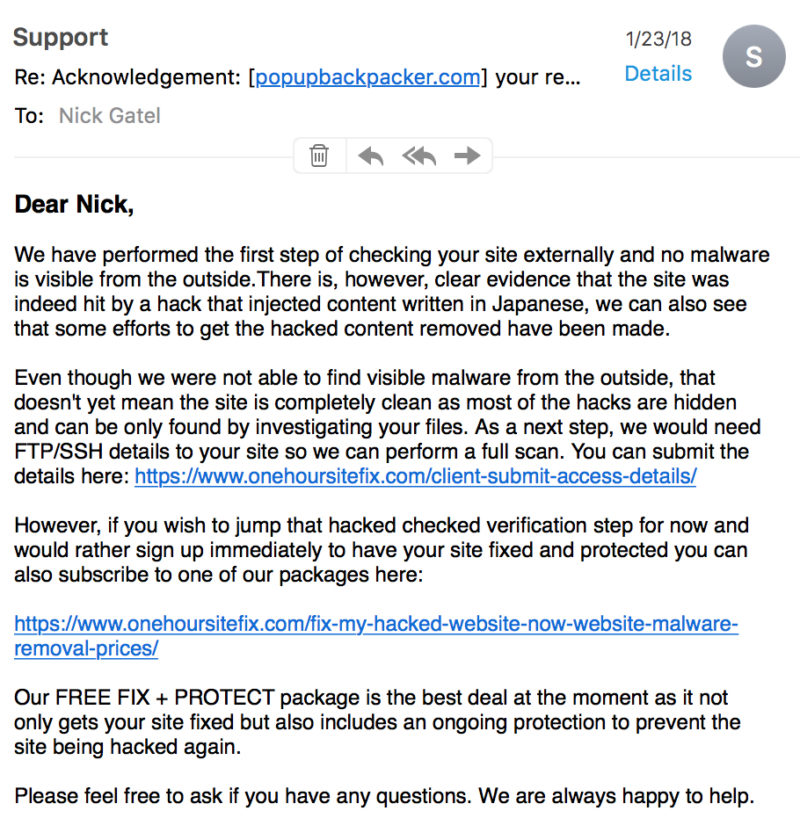
Email #1
And then I got this follow-up email:
Email #2
However, at this point I was a little leery, even though I had read some really good things about this company, which by the way, is located in London, England. Then I got a second email. This one said that externally there was no visible malware, but there was clear evidence that a hack had added content written in Japanese. They recommended that I provide them with my User Name and Password to the files stored on my server so they can directly access everything, or I could go a head and purchase one of their packages. At this point, I wasn’t confident that purchasing a package would solve my problem. So I gave them the log-in the server site address and log-in credentials.
Now, this isn’t as scary as it sounds. My website is hosted on an external service I pay to use, so there is no personal information there. Plus I wasn’t concerned that this could be some sort of scam to damage my website, because my site is backed up daily and it is easy for me to restore it. So I gave them the information.
I received a couple emails with status updates on the scanning operation. Then I received an email with the results of the scan.
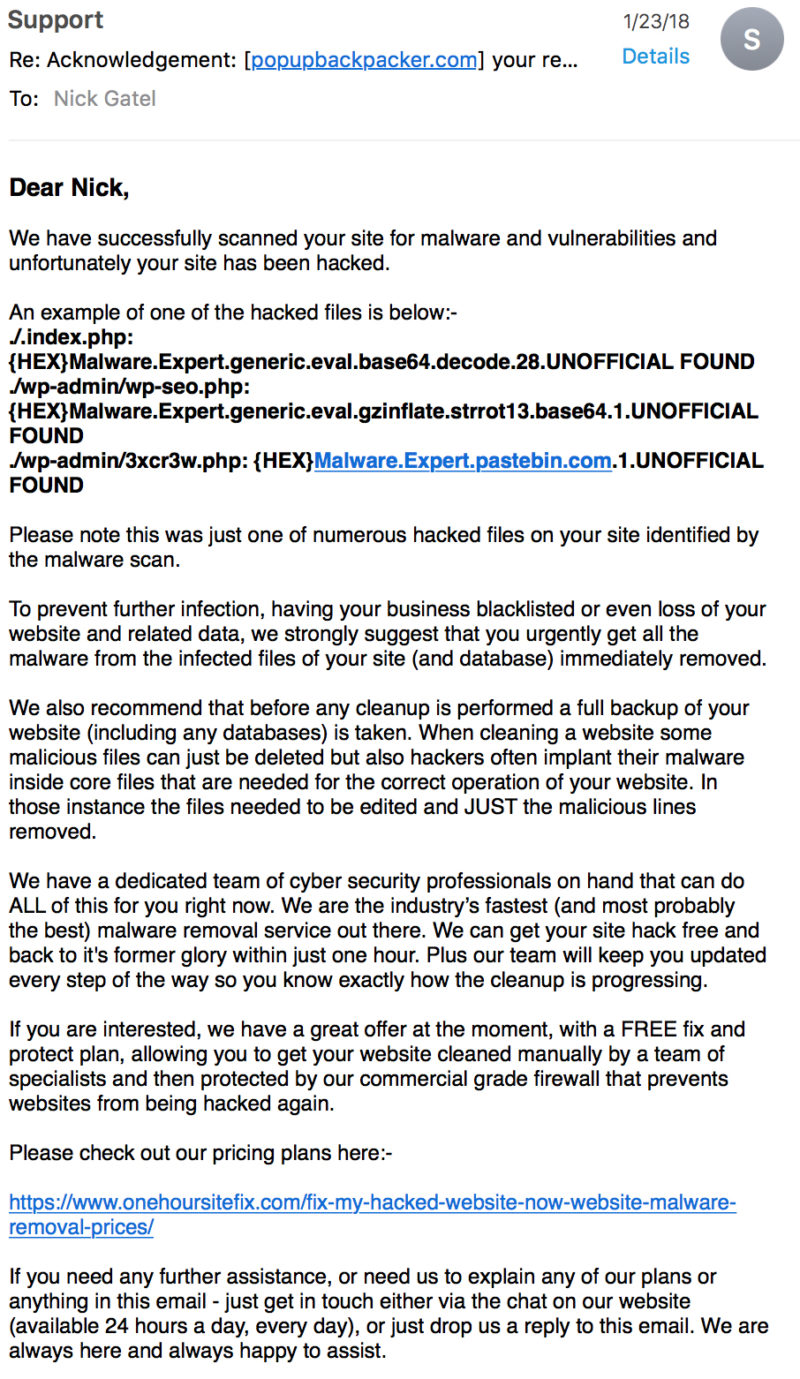
Email #3
They had found a lot of stuff and stated they could fix it. A link was provided with pricing. Basically $250 to fix the problems, or a free fix if I subscribed to their protection service (a firewall). The service runs $29.99 a month or $299 if a one year subscription is purchased. It was 11:30 at night, so I decided to sleep on it because who wants to spend that kind of money when one is the victim of a crime. Plus I wanted to see if the company would continue to contact me with a ‘hard sell’ strategy.
When I got up in the morning there were no new emails. I checked the files they referenced and verified their findings, and did some more research on them. Still, I was hesitant to spend money to undo what had been done to me. Finally at around 2:30pm I went ahead and purchased the yearly plan for $299.
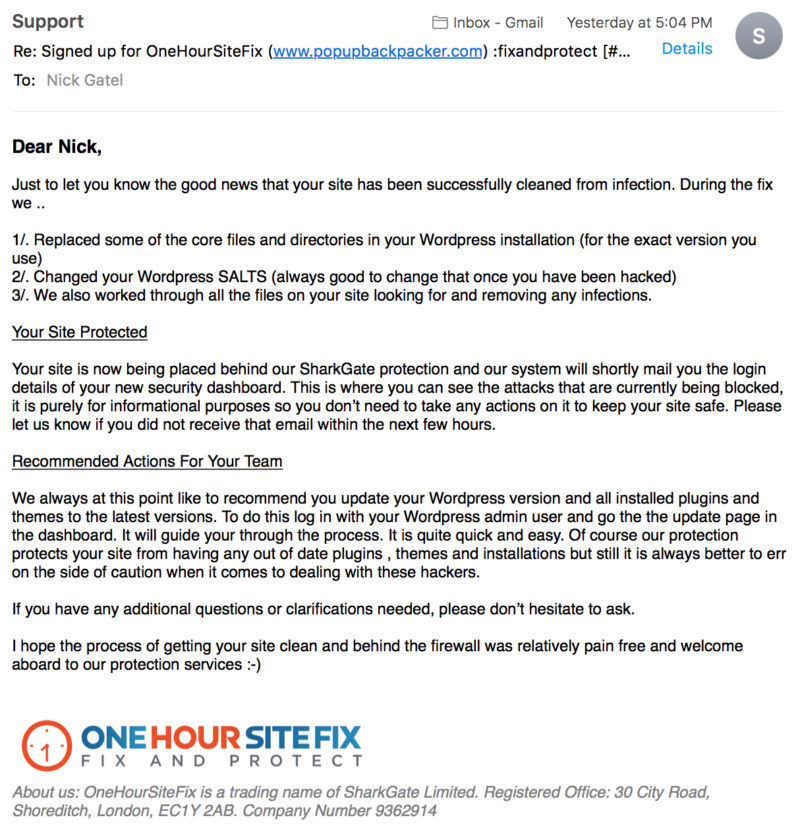
Immediately they went to work and we had several email exchanges for a couple of hours. Then at 5:04pm I got this email.
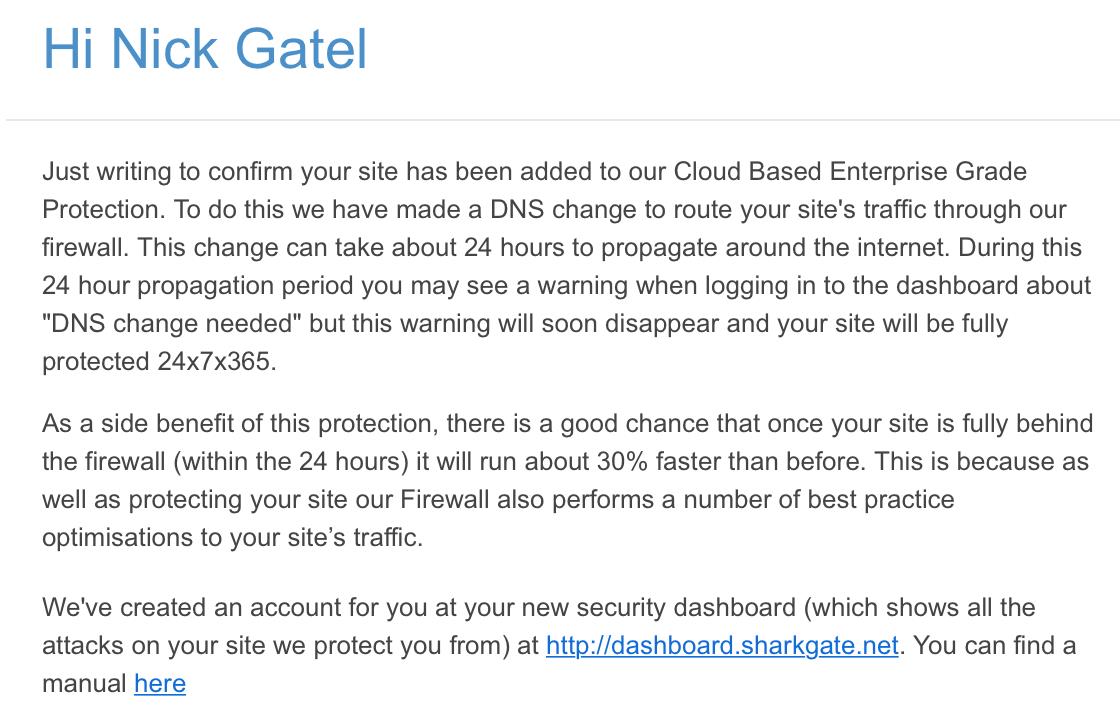
Email #4
And then this email:
Email #5
I didn’t include all of the email because it has some log-in information that needs to be kept private. The Firewall dashboard looks like it will be a handy tool for me, although it won’t start feeding data for 24 hours.
After this was all said and done, I went back to the Google Console to check and see if everything was working and if the hacks were gone.
Yeah! Yeah! Yeah! Fixed! Fixed! Fixed!
Best Practices
Here are some things everyone who has a blog or website should do.
- Make frequent backups. I have a service that backs up my site daily (JetPack for WordPress).
- Immediately update any software updates and plug-in updates. This mean you have to go to your website’s administrative dashboard and check it often!
- Get extra security for your site. I did have some ‘free’ security plug-ins, but what you get is what you pay for.
Bottom line is ONEHOURSITEFIX is awesome! If you have a blog or website, go buy there service. You don’t want to wait until your site gets hacked like mine just did.
Shameless Plug
Okay, now I have to pay for this. If you are planning to buy something from Amazon, why not use the Amazon link here. Doesn’t cost you extra, and I get a little commission to help pay to run this site.
Here’s a picture of the Amazon link. If you are using a desktop, the link is on the right hand of the screen, on a smartphone you’ll have to scroll to the bottom. Thanks, in advance!
Final Thoughts
Almost everyone I know has been a victim of crime. And we just put up with it. In this post on Bike Security I made some observations and recommendations.